Tutorial
OpenVPN Access Server is a full featured SSL VPN software solution that integrates OpenVPN server capabilities, enterprise management capabilities, simplified OpenVPN Connect UI, and OpenVPN Client software packages that accommodate Windows, MAC, and Linux, mobile OS (Android and iOS) environments. In short: OpenVPN Access Server is 'almost free' and 'just OpenVPN' (Community Edition) is totally free. However, they are configured in different ways. Open AS has indeed a web interface that simplifies (a lot) the tasks for setting it up. Open CE on the other hand, has to be configured by editing some configuration files.
Status: Deprecated
This article covers a version of CentOS that is no longer supported. If you are currently operating a server running CentOS 6, we highly recommend upgrading or migrating to a supported version of CentOS.
Reason:CentOS 6 reached end of life (EOL) on November 30th, 2020 and no longer receives security patches or updates. For this reason, this guide is no longer maintained.
See Instead:
This guide might still be useful as a reference, but may not work on other CentOS releases. If available, we strongly recommend using a guide written for the version of CentOS you are using.
Introduction
VPN, or virtual private network, is a secure method of connecting remote internet resources together as if they were under the same LAN. OpenVPN is a popular implementation that works on Linux, Windows, and Mac operating systems and can be utilized to create complex, encrypted networks between physically dispersed servers.
The OpenVPN Access Server is a solution built on top of traditional OpenVPN that is used as a complete portal for managing connections, users, and interfaces. It provides the underlying VPN instance, a web interface for managing the suite, and a client that can be used within a web browser.
In this guide, we’ll install and configure the OpenVPN Access Server on a CentOS 6.5 VPS instance.
Download and Install Packages
We can obtain the OpenVPN Access Server package for CentOS from the project’s website.
Right click on the package that matches your version of CentOS and your machine’s architecture. Select the “copy link address” item or whatever option is closest.
On your CentOS droplet, download the package with curl -O (that’s the letter “o” not a zero) followed by the URL you copied from the page. In my case, this turned out to be:

When the package has been downloaded, you can install it with using the rpm command:
After installing the package, an administration account is created called openvpn. However, no password has been set.
Set a password for the administrator’s account by typing:
Now, the command line configuration steps are complete. The rest of the guide will focus on configuring options through the web interface.
Accessing the Web Interface
We can access our VPN portal by going to our server’s IP address or domain name, at port 943. The server operates using TLS, so we will need to specify the https protocol.
For our initial interaction, we actually want to go to the administrative interface, which is the same, except ending with /admin:
<pre>
https://<span class=“highlight”>serveripor_domain</span>:943/admin
</pre>
You will get a warning that the site’s SSL certificates are not trusted:
This is expected and perfectly fine. All that this is telling us is that OpenVPN is using a self-signed SSL certificate, which is not trusted by default by our browser. We can click on the “Proceed anyway” button or whatever similar option you have.
Note: If you are unable to connect to the web interface, there’s a chance that OpenVPN is bound to the wrong network interface. You can verify this by typing:
If the response does not show your server’s public IP address, you will need to manually reconfigure it by typing:
Delete the current configuration by typing DELETE at the prompt. Next, accept the license agreement and press ENTER to mark this as the primary server. In the next prompt, select (1) all interfaces: 0.0.0.0 to bind to all interfaces. This will ensure that the access server is available in spite of a bind error in the OpenVPN installer. Press ENTER to accept the default values of the remaining prompts.
After reconfiguring, you should be able to access the web interface after accepting the SSL certificate in your browser.
You will be presented with the admin login page. Use the username openvpn and the password you set for this user:
You will be taken to the OpenVPN Access Server’s EULA, which you will have to agree to if you wish to continue:
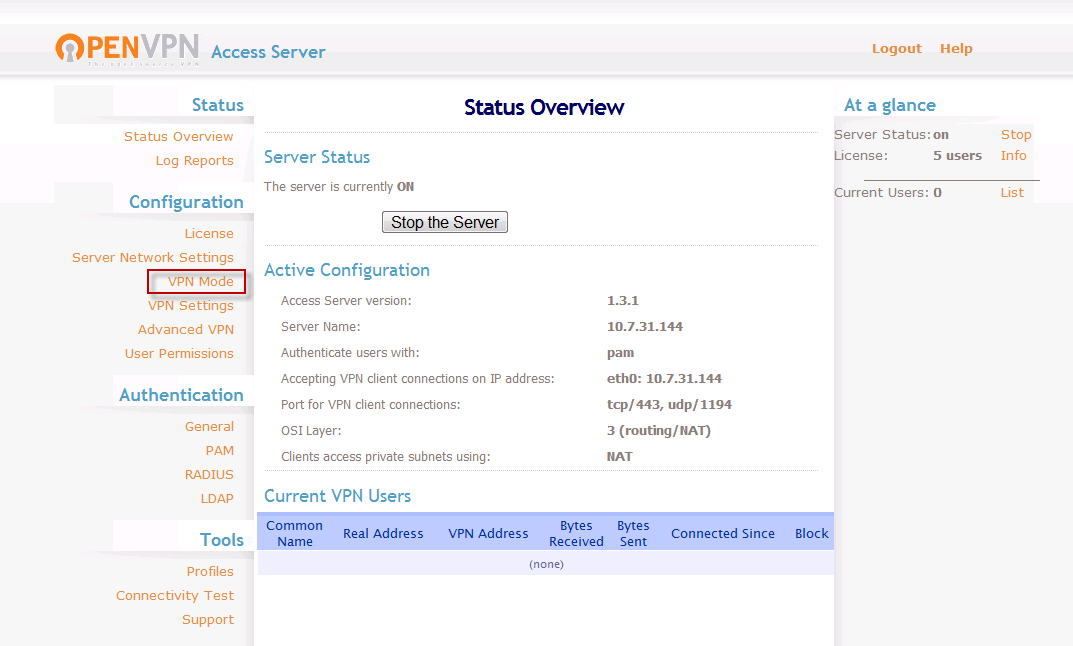
Once you log in, you can see the administrative interface, complete with some useful at-a-glance stats on the landing page:
Here, you can configure your VPN server. The access server separates the web interface and the actual VPN access and each can be configured independently.
For instance, if you go to the Server Network Settings in the left-hand menu, you will see a page where you can configure the port and interface that each component operates on. You can also specify the address pool that will be available to the clients.
Another thing you might want to do is add users and configure the authentication methods. You can add VPN users that match your system users, or add users that you might be controlling through an LDAP server.
Logging in as a Client
When you are finished configuring things as an admin, you can visit the client portion by going to your IP address or domain name followed by port 943:
<pre>
https://<span class=“highlight”>serveripor_domain</span>:943
</pre>
You will have to type in a username of a user that you have configured VPN access for:
If you the user that you logged in as has been designated as an OpenVPN admin account, you will see an “Admin” button that can be used to take you back to the admin control panel. Either way, you will be taken to a page that will allow you to download software for your client to connect to the VPN server:
If your desktop is Windows or OS X, or if you have an android or iOS device, you can download an OpenVPN Connect client that will operate within your browser. If your desktop is a Linux machine, you will be asked to download the normal VPN client.
You should follow the directions of the client of your choice. If you are using the Linux client, you’ll need to download the connection settings profile by clicking on the “Yourself” link:
Using the regular Linux openvpn client, you can connect using something like this:
Conclusion
Now, you should have a portal that can be used to configure your VPN access. This is an easy to manage interface that can be set up once and configured on-the-fly. It automatically generates valid configuration files for your users to connect to the server, which can save a lot of headaches with explaining how to configure access.
<div class=“author”>By Justin Ellingwood</div>
Introduction
OpenVPN is an open-source third-party software that uses virtual private network (VPN) techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and provides remote access facilities. It uses a custom security protocol that utilizes SSL/TLS for key exchange.
OpenVPN uses the client-server connection to provide secure communication between the client and the internet. The Server is directly connected to the internet and the client connects to the Server which eventually connects to the internet.
The Authentication on OpenVPN is based on pre-shared secret keys, certificates and username and password of the end user. It releases certificate for every client connected to OpenVPN Server.

In simplified language, if you do not want to expose your infrastructure to be publically accessible, then we need to implement a VPN. In order to access all the servers in the private network, we need to be connected to VPN Server first.
In this blog, I will show you the steps to install and configure OpenVPN Server and how to connect to your private servers (using the private IP address). For our implementation, We will be using an ec2 server on AWS Cloud.
Pre-requisite.
AWS Account – To Launch and Configure OpenVPN on ec2 Server.
VPC with Public and private Subnet.
Launch an ec2 Linux instance and login to it to begin the setup process. instance type will depend upon the load on the VPN Server.
Also, make sure that the following ports should be open on the security group
- Custom UDP and TCP rule: 1194
- SSH: 22
- Custom TCP rule: 943
- HTTPS: 443
Install NTP and wget,
Check whether the system clock is synchronized or not by using “timedatectl” command.
Now download the OpenVPN Software package from the link. You can download based on the distribution of your OS. We will be using Ubuntu 18 for this setup and at the time of writing this blog, the latest version for OpenVPN was 2.6.1.
Once you have downloaded the package, execute it using below command.
The output will be something like this,
So now we have to set the admin password for your OpenVPN Server, execute the below command,
Now, Login to the OpenVPN Access Server as an administrator.
It will Show the connection is not secured, as it uses the self-signed certificate. Just Click on Advance and Click on add exception and Confirm Security Exceptions
Login with your Username and password which you have set from the terminal above.
username: openvpn
pass: your password.
- Click on Agree to Accept the Licence agreement. You can now see the Admin Control panel.
- Click On, Network Settings, and Provide the following details, though these details are available by default. Just cross verify it.
- Hostname or IP Address: IP_of _VPN_Server.(Public IP.)
- Interface and IP Address: Enable the Server interface (not listen on all interface)
- Protocol: Both (Multi-daemon mode)
- Under Admin UI: enable interface (eth0: IP)
- Under Client Web Server: Enable Use the same address and port as the Admin Web Server
Now Click On VPN Setting Under Configuration and Under the routing Section Select Yes, Using NAT and provide the Private Subnet from which all client should be given access to.
Also, You can enable the client traffic to be routed from VPN. but it’s better not to route the client traffic from the VPN Server.
Click On Save Setting and Click Update Running server.
Now, let’s add a user and try to establish a connection to your private servers using that user’s credentials.
Click on User Permission under User Management.
Provide the name of the user and check on admin if you wanted to grant the admin access to him/her. Here we will add a normal user.
You can also enable Require user permissions record for VPN access for logging. (user login activity.)
Click on Save Settings and Click Update Running Server.
Note: Click on More Settings and set the password for the user.
Local Password: Your Password.
Now lets login as a normal user, https://public_IP_of_VPN_server (don’t use /admin).
It will appear like below in the screenshot.
Provide your credential there and download your client.ovpn file to connect to OpenVPN. Click on Yourself (user-locked profile) to download client.ovpn file.
Now, once you have downloaded your client.ovpn file try to connect the OpenVPN Server by executing below command. (Only when you have Linux client/ Using Ubuntu/other OS)
Provide your username and password and press enter. you will be connected to OpenVPN Server once the initialization sequence completed.
Now, try to connect to your servers in the private network, you should be able to directly login to your private instances using the private IP address.
Note: Do not close the terminal once connected, this will break your VPN connection.
Above command will only work for the Linux Client
For Windows user, Download the Windows clientand connect from it.
We can also connect to OpenVPN Server Using the network manager, which We will see in the next blog.
Openvpn Access Server Ubuntu
You May Also Like!!
If you Like Our Content here at Devopsage, then please support us by sharing this post.
Please Like and follow us at, LinkedIn, Facebook, Twitter, and GitHub
Openvpn Access Server Saml
Also, Please comment on the post with your views and let us know if any changes need to be done.
Thanks!!